![]()
Press
![]()
Links
Subscribe to Mailing List
User Tracking
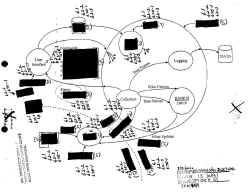
The local inhabitants of the space watch the system replay events and statistics on a nearby screen nearby. When a remote user logs in, a klaxon alert will be made and the system will pan and tilt as the remote user operates it. Local viewers will see the processing and acquisition of remote user data as well as the video feed from atop the shockwave cannon. Of course local user on another networked computer can drive the system and target individuals.
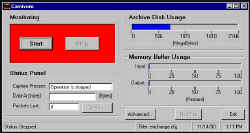
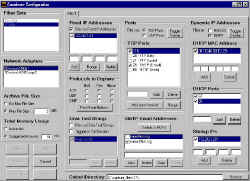
During the operation of Gallery Shooting Gallery, a detailed log is also made (and displayed publicly) of the remote individualís computer properties by probing various ports and access patterns on their system without their knowledge in a Carnivore like style. Carnivore is the US Governments best weapon at surveillance of an individuals network activity and traffic. These are low level probes to obtain information far beyond what is typically contained in access logs. All information will be provided for public consumption on the web at a later date/time.